An overview of email security, identifying suspect emails, socially engineered threats and how best to deal with them.
It‘s no secret that having an online presence while mandatory in the technological world we live in today, is also laden with a million and one security apprehensions, and the statistics surroudning failure to secure email solutions is unsettling. We’ve compiled a few pointers that we hope you take into consideration, promoting a safer and smarter work ethic helping your business navigate the “gotcha’s”, “captcha’s”, “spoofs” and “phishing attempts”.
More Haste, Less Speed
Acting too quickly and without due diligence, focus and attention to detail will result in avoidable mistakes and thus require even more time to complete tasks satisfactorily. While mistakes can be unmade in most scenarios; when it comes to email security, we’re all only one potential click away from utter devastation. Take a moment to review the emails you’re receiving, especially if they have links or attachments in them. While we’ll detail below some tricks to spot the fakes, none will matter if you’ve not taken the time to check!
What is Spoofed Email?
Sent on behalf of, altered email addresses with seemingly valid “display names” and then a “complete spoof” are the three most common types of email spoofing we see.
Sent of behalf of is as describes, an email that’s sent on behalf of someone you may know or trust, but the original sender is just pretending, “spoofing” these rights. There’s not a chance that I’ve given admin@sxtzjt.cn rights to my email address, but as per the screengrab below, it looks like I have. They’re modifying parts of the email hidden to the user but used by the system to display this information to make it look like they’re sending on behalf of me. This spoof could be made much more lethal had they pretend to be for example a PA to a Director, with the email being sent to someone in Accounts trying to rush through a payment for some Amazon gift cards. If the Accounts user just rushes the request and doesn’t stop to ask the PA, or even the director to confirm this request via direct email or other communication means, the scammer has just made off with £100’s in gift vouchers. Avoidable if you know what you’re looking for:

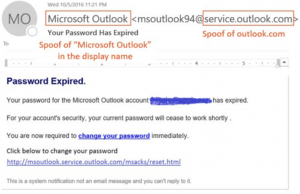
Altered email addresses again are self-explanatory, whereby an email address has its display name set to look legitimate, but the actual email address behind it is not from a trusted source. In the example below the first name “Microsoft” last name “Outlook” is trying to make it look like my account password has expired and needs renewing, yet if I click any links they’ll likely take me to a website that looks like a Microsoft site, will ask me to enter my old password and then enter my new password twice, but the website will be a fake version of a Microsoft website, and the passwords I just typed in are now known by hackers and are associated with my email addresses. Before I could even check my main websites where those passwords may be used, the hackers will have software written to try 1000’s of websites with the password I’ve just given them and my email address as the username, and if successful in login, change the password to lock me out. This is avoidable if you either edit your outlook profile view settings to always display a senders email address or if not, the user manually moves their mouse over the display name of the sender to have the full email address appear as a balloon “pop-out” message:
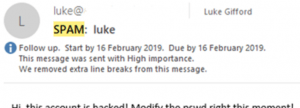
A Total Spoof would be where the data stored in the email “Headers” (hidden when just viewing the message content, but is something you can see when expanding the properties of the email), to make the email look like its actually from me. There are tools and processes we can review and implement to prevent this from happening. In the instance below the hacker is trying to scare me into giving them money to get them to stop “hacking” me, but the concept of spoofing a person or a company can expand beyond scare tactics of emailing a user with their own email address as the sender. Hackers can use social engineering (see further below) to receive direct emails from companies, providing them with a template to mimic ready for when they send out spoofed emails, even going as far as including images of the person they’re spoofing if “meet the team” pages exist on company websites.
Basic English
Instead of skim reading, barely processing the content and just trusting a sender; pay attention to the wording of the emails you’re receiving. It‘s very common for non-native English-speaking hackers write out the wording of their emails in their innate language then use google translate to flip it over to English, this results in some very odd wording that helps identify emails that are not to be trusted, this is an easy spot and greatly improves your email security:

Attachments
Please, if there‘s anything you take away from this advice listing, please pay attention here. Disable “Auto Macro” in your office suite applications. The most common delivery mechanism for viruses, malware and worst of all ransomware is an Excel spreadsheet, Word file or PowerPoint presentation that contains a macro sending whoever activates the macro off to the internet to download and install malicious software. Stopping macros from automatically running outright prevents this. Simple go to File > Options > Trust Center > Trust Center Settings… > Macro Settings > ensure “Disable all macros with notification” is the highlighted selection > Click OK.
Hyperlinks
Links to websites can be hidden in many ways, far too many to list here. However, the process of checking is the same for all hyperlinks. If your cursor changes to suggest active content in the email you’ve received, leave the mouse hovering over the content for a couple of seconds, and your email client should allow for the full URL to pop up, revealing the true destination of the link you’re about to click. Links can be applied to anything in the emails, emails can even be formatted to make it look like a file is attached, but in reality, the start of the email before any salutations is just a well–formatted image hyperlinking to a malicious site. Take a moment to mouse over those links; make sure they’re safe before you click on them.
Dates and Times
Often overlooked is the scheduling of these hacked/spoofed emails. Would that customer you’ve not heard from in months really be emailing you at 05:00 on a Bank Holiday Monday? Or is the person sending the dodgy email in a completely different time zone where it‘s more like 12:00 and they’re not taking into account the time difference or other counties national holidays?
Additional Email Security for Financial Transactions
If you want to have high ranking officials within your company sending accounts team members a move request of company funds, play it safe and arrange for a second layer of security. Have a prearranged and agreed–upon code word, call and response request or a statement that must be recited and is only valid for the current day/week/month. Any financial requests should be invalid if missing from the request. As simple as it sounds, we’ve known this process save several clients of ours from financial loss.
Final Thoughts
There’s only so much defensive security software can do for your systems when it comes to email security, regardless of how many security features it has to offer. A swiss army knife is only as useful as the person wielding it. Thank you for taking the time to read these pointers, if you’d like any of the above to be explained in detail or you’d like advice on how to improve your business’ cybersecurity, please get in touch we’d be glad to help, as what we do today, secures your business for tomorrow.
